A way to enforce good practice and standards is by Azure Policy. As stated by Microsoft “Azure Policy is a service in Azure that you use to create, assign, and manage policies. These policies enforce different rules and effects over your resources, so those resources stay compliant with your corporate standards and service level agreements”. Pretty important stuff if you ask me.
This does cover vast amount of different services, but what polices exist for SQL related services? Under Azure Policy I filter on “SQL”. You can scope this to a resource group if you desire.
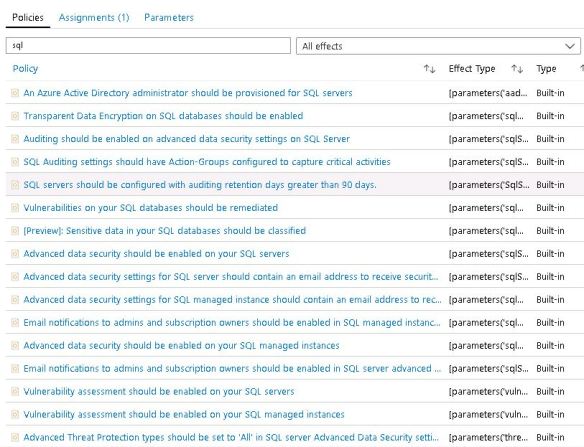
This is a just a snippet, there are more. However I want to see when a policy condition has not been met.
I find this from the main dashboard.
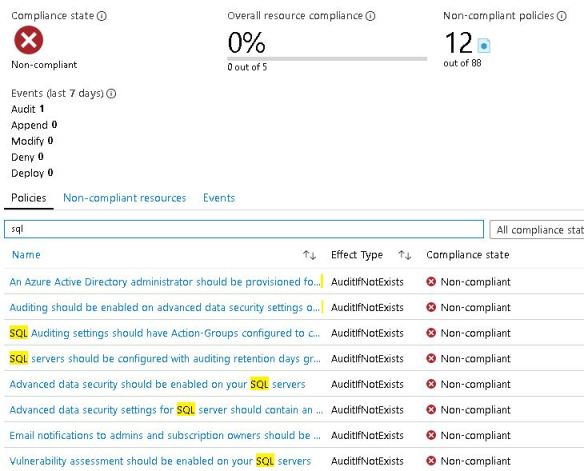
Here is a list that I must work from and fix for my environments. I suggest you guys have a look into this too to build some standards and governance.
My list to fix non-compliant rules includes:
- An Azure Active Directory administrator should be provisioned for SQL servers
- Auditing should be enabled on advanced data security settings on SQL Server
- SQL Auditing settings should have Action-Groups configured to capture critical activities
- SQL servers should be configured with auditing retention days greater than 90 days
- Advanced data security should be enabled on your SQL servers
- Advanced data security settings for SQL server should contain an email address to receive security alerts
- Email notifications to admins and subscription owners should be enabled in SQL server advanced data security settings
- Vulnerability assessment should be enabled on your SQL servers
- SQL server TDE protector should be encrypted with your own key

you say that “Auditing should be enabled on advanced data security settings on SQL Server”. What do you use that for, and how?
LikeLike
If you go to security section on the SQL Server in Azure Portal you will see Advanced Data Security. scroll to the bottom, you will see advanced threat protection settings. when you enable it, it says “enable auditing for better threats investigation experience”. The auditing element here is so that the events(for threat protection) get written to a storage account for future access which I usually do.
LikeLike
Thank you very much for that explanation. I’ve enabled it, and I get a weekly Vulnerability report email. So the history log is really for my manager/successor, to see if I did my job?
LikeLike
yes so if you have enabled auditing it will log the entries (I setup a storage account) to investigate current / past entries.
LikeLike